There is much I have learned since my last article (now outdated) on what makes a good browser setup. This article aims to be a more concise and pragmatic revision of my thoughts and recommendations as was detailed in my original article. This guide still assumes a basic understanding of software and a desire for online privacy against tracking and targeted advertising.
Hopefully, this will also be much more straightforward to follow.
It's important to determine what you actually want in a browser. What you are okay with and what you are not with. Do you want simplicity and reliability? What about performance and customisability? Do you want total control with your browser? For me personally, I act on a principle of minimalism and strengthening privacy where it is practical. Less is more. I aim to mitigate unnecessary connections and avoid using or installing anything I don't need.
Incidentally, if you're looking for maximum privacy and anonymity, this is not the article for you. For an autistically comprehensive guide, checkout this place instead.
First of all, what browser choices do we have? The only decent options rely on one of the three major engines: Blink, Gecko and Webkit.
What environment you work with will determine the best browser(s) of choice. With that being said, Chromium offers the best all-round product for me, because it has stronger support for multiple platforms compared to Webkit, and stronger security compared to Gecko. If you only care about functionality, Opera and Opera GX - based on Chromium, are feature-rich.
If you're looking for a "best browser" in terms of (core) functionality, security, privacy and ethics, then I hate to disappoint you, but there isn't one. It's not even close, to be honest. There are plenty of reasons to criticise every browser (and/or the companies developing them). When it comes to basic privacy, the inherent "exposed" nature of the internet is pretty much solely responsible for causing this whole mess in the first place, but I digress.It is for this reason that most of the extensions I install are on my secondary browser. Only a small group of individuals maintain these versions of Chromium, and apparently, the security of this is slightly worse than Chrome, but given I don't use it for anything sensitive, that hardly matters.
Then there's Brave - my primary browser, which is backed by a company and maintains Chromium's security model with timely updates. Security is necessary when you want to handle tasks such as accessing your bank account. On top of maintaining Chromium's security model, Brave provides a variety of useful - and not useful, features out of the box, which I shall gloss over.
Brave's content blocker (apparently based off of uBlock Origin) is pretty good at blocking ads. It hardly improves privacy, but it has one significant advantage over all content blocker extensions . It is built-in. In other words, all Brave browsers feature this, so with no need to install another content blocker (and assuming you don't change the shield's settings), you are not increasing browser entropy.
This is... a convenience feature. I - nor Brave, recommend this for anonymity, but it is still useful in the rare case where you need to grant website permissions while hiding your IP address. This is something that - in my experience, is not supported in the Tor Browser.
You probably don't need a VPN. Seriously. This alone has given me enough headaches, so I'll spare you the trouble. Don't bother.
From what I understand, Brave's primary business model is advertising in their browser and in their search engine. This is opt-in and allegedly does not involve privacy-invasive practices such as tracking. As an incentive, the user receives Basic Attention Tokens for viewing ads. While I appreciate Brave's approach, I do not like advertisements on principle, so I don't opt-in.
Web3 is a buzzword and frankly not something I care for. Brave offers a cryptocurrency wallet, which you can use for handling BAT and other stuff. Though, if I had any cryptocurrency, I would opt for a more dedicated wallet for security and compartmentalisation purposes.
To avoid worsening Brave's fingerprint resistance, I try not to change any of the settings that directly influence websites - which are mostly from Brave's Shield settings. There is one exception, however.
You should set the WebRTC IP handling policy to "Disable non-proxied UDP". WebRTC is a convenience feature that will leak your IP address in the event you are using a VPN (if ever).
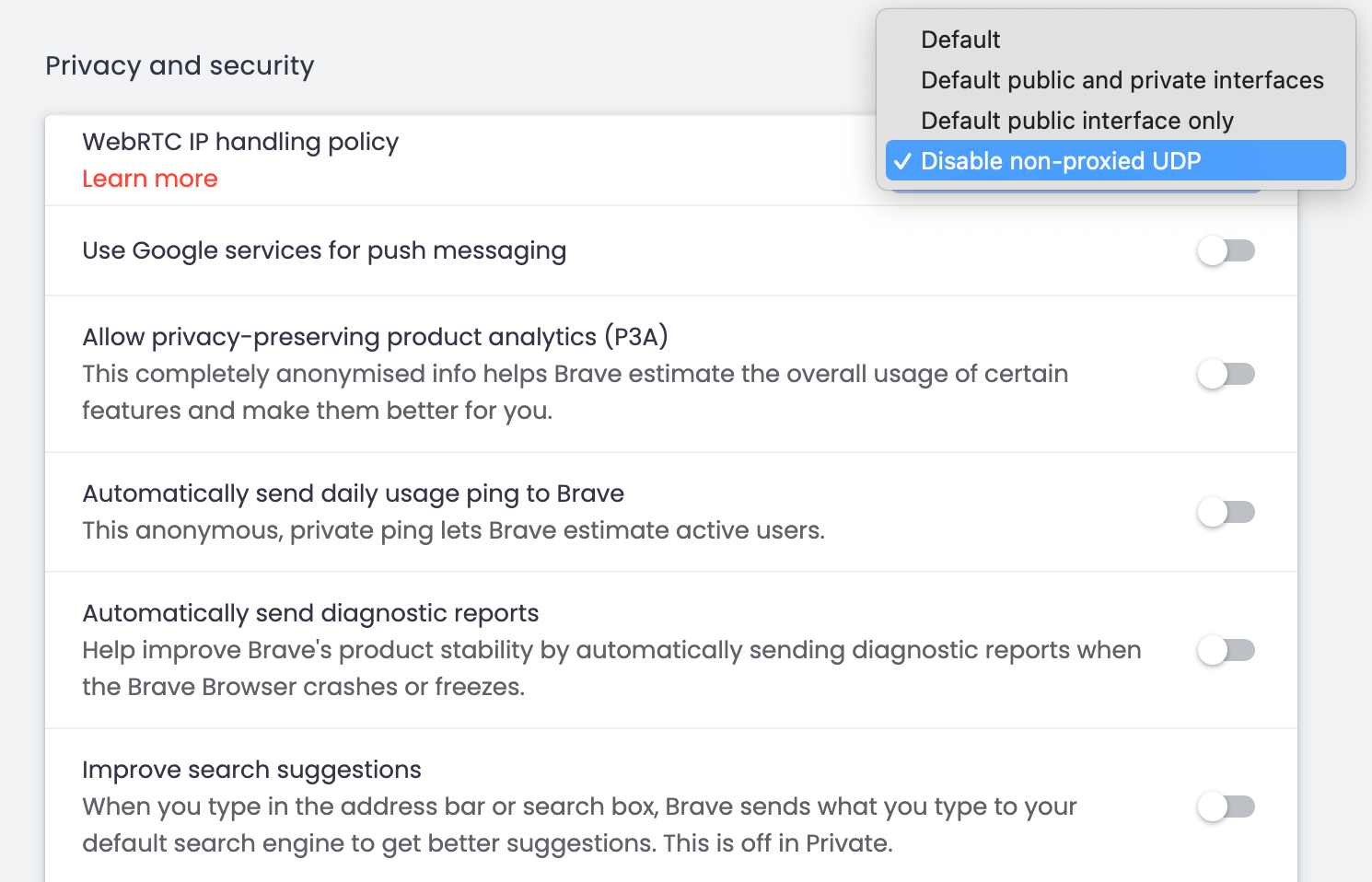
Incidentally, many other Chromium browsers don't support optional WebRTC. In such cases, you'll need to install a dedicated extension such as this one. But again, this is contributing to the issue of adding more extensions.
I leave all shield settings as default, as it provides sufficient ad blocking, and any manipulation of these settings will separate your browser from the most common Brave setup (default), increasing entropy. This makes it easier for fingerprinting methods to identify you.
I also disable all settings that would optionally send data to Google and Brave. I do this for the purpose of minimising unnecessary connections.
It's worth noting that if you use Google features such as Safe Browsing or push messages, you will connect directly to Google servers. I don't like Google's anti-privacy practices. But even so, a simple connection like this is hardly a reliable metric to use for tracking. So if you think you won't be able to reliably identify malicious actors on the web, my suggestion is you enable Safe Browsing.
In addition to your default search engine, you can also search on specific websites using keyword searching.
Essentially, I can search on a specific website via the (search) omni-box with just a single letter.
This is keyword searching in action:
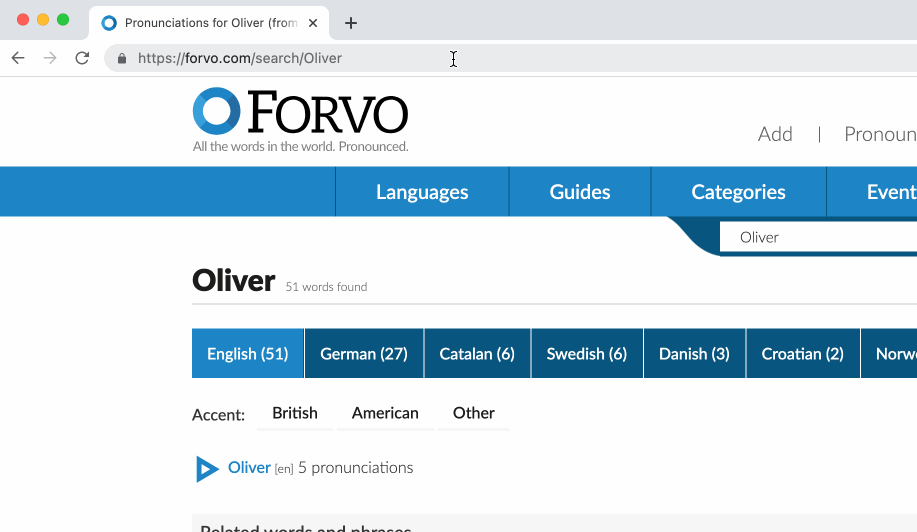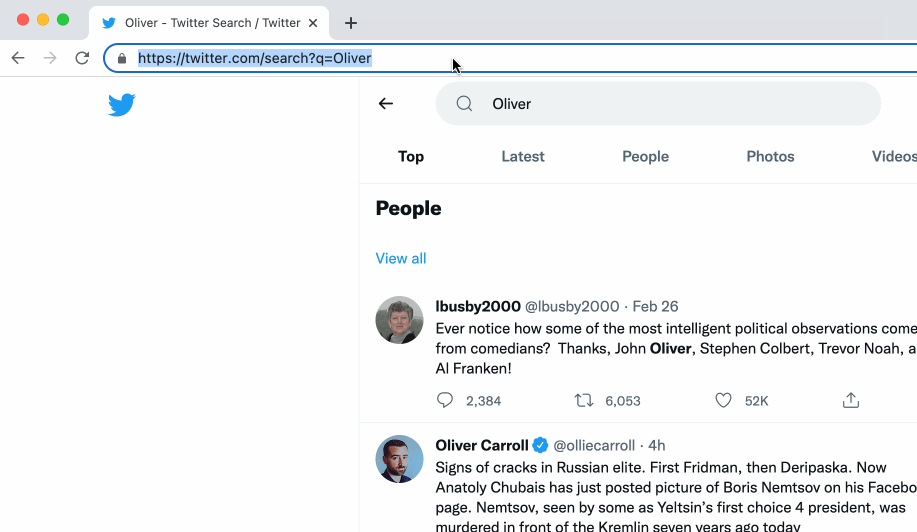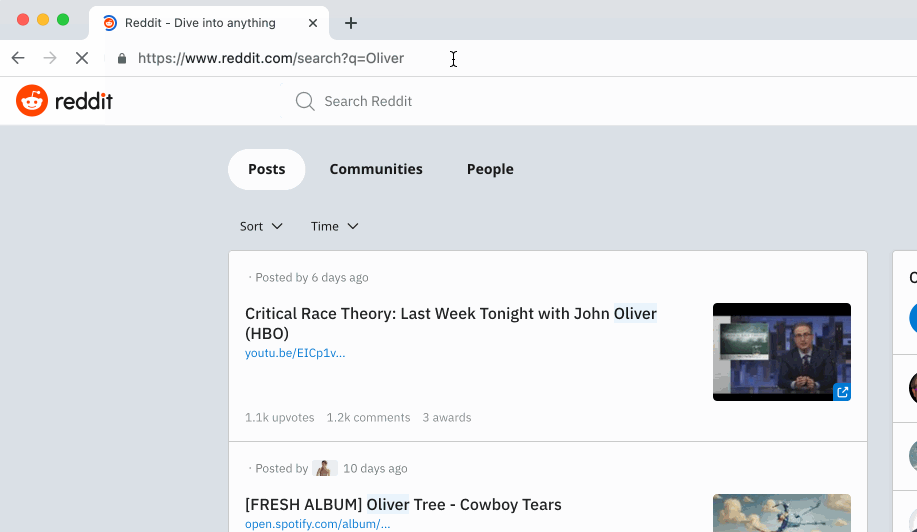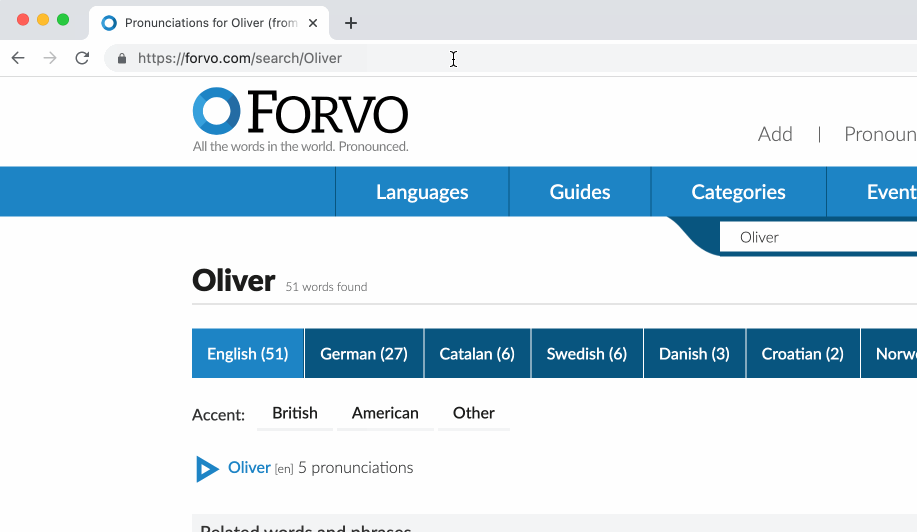
Anyone who's ever used DuckDuckGo's !bangs will be familiar with this underrated feature. However, keyword searching is advantageous for two reasons:
Chromium will automatically set these up for you if it thinks it can, albeit using the full name of the service as the keyword. Single character keywords are much more efficient. Just avoid using single-letter words like "a". Then it's simply a matter of setting up the correct URL for searches.
Here's an example of reddit and Twitter:
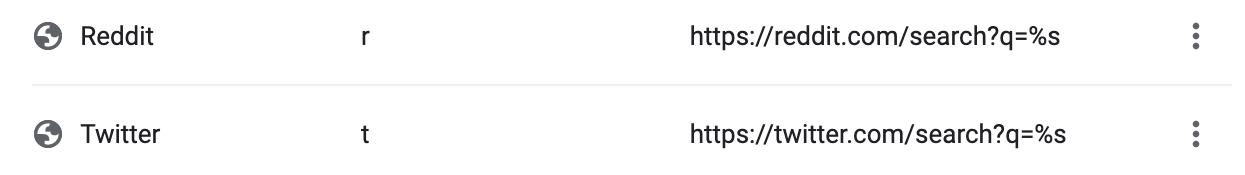
Here, the %s at the end of both URLs are the placeholder for your actual search query.
As much as I love extensions, it is against our interest to needlessly pile them on. Otherwise, we risk increasing attack surface and entropy in the browser, which is counter-intuitive if you're looking for security and privacy respectively.
Brave offers quite a few features out of the box, like Brave shield, so there isn't much reason to install extensions. Though if I were using another browser, my first choice for a content blocker would be uBlock Origin. I have this installed on my secondary browser, in fact.
(Note that uBlock Origin should not be confused with uBlock, which is a different content blocker)
See Also:
Mobile devices are more limited in choice. On iOS, the only reasonable choice is Safari and maybe the Onion Browser. On iOS, browsers are forced to use the Webkit engine, so there's little point in using other browsers, unless you care about syncing bookmarks or whatever.
Android gives more freedom, but I still suggest using a browser based on Chromium. Gecko has flawed security on Android.
There is an official Tor Browser for Android as well.
For most Android users, Brave is what I'd recommend for security and privacy.